Technology
The TripleCheck technology was first released to public in 2013 and is continuously improved with the feedback from customers. The main product is called Xray, which is currently on its second generation of releases.
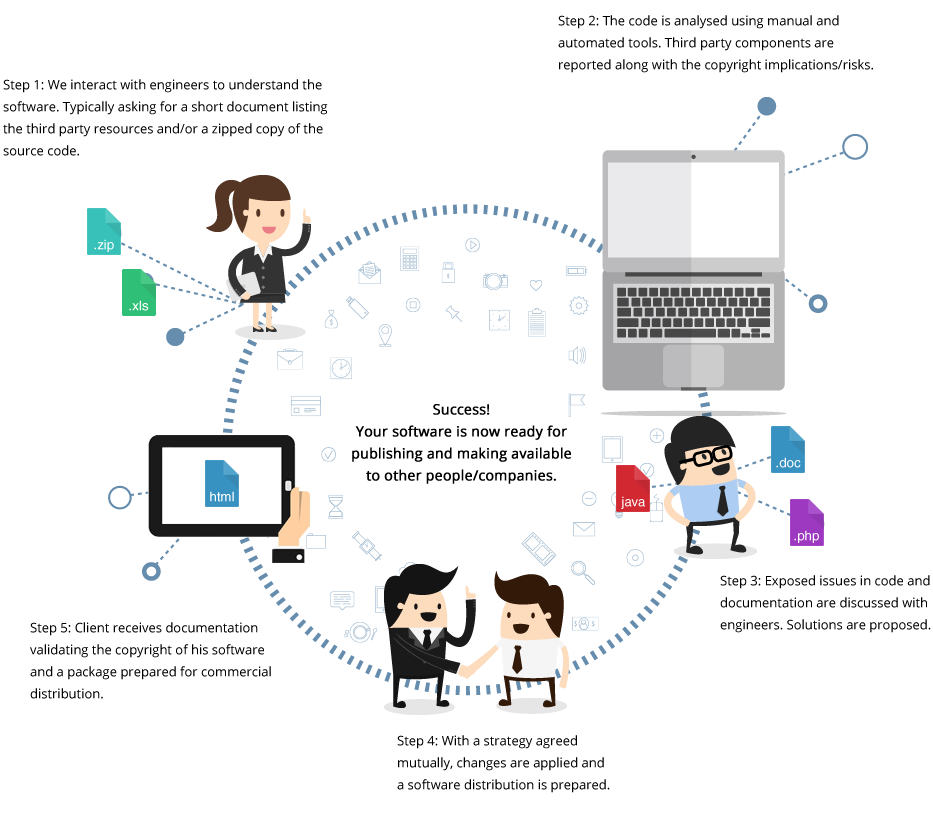
TripleCheck as a forensic auditor, performs the following activities:
- • Collecting an offline archive of publicly available software
- • Detecting license terms on the software surface
- • Detecting software plagiarism
- • Generating software inventory lists (also known as Bill Of Materials)
The offline archive spans to about 2.5 petabytes of software collected from diverse public sources on the Internet over the years, namely github, sourceforge, bitbucket, stackoverflow, among others. This data is archived inside its own premises, from which are built the fingerprint databases that are later used for the offline matching of source code files and snippets.
In 2018, the TripleCheck Open Source archive amounts to 1,9 billion file fingerprints and 1,2 billion code snippets (methods, functions) from 55 programming languages. Technology-wise, only TripleCheck has the forensic capacity for identifying similar binary files in large scale, in addition to the exact fingerprint matching based on SHA1.